

Mobile Device Management options included with Microsoft 365
For many of us, phishing emails have become a nearly daily occurrence. After all, phishing is a very effective and lucrative attack mechanism for malicious actors. But, businesses and individuals quickly began responding to phishing attacks with implementations of two-factor authentication in addition to user education and better spam/security filters. It is problematic and often costly for attackers to infiltrate accounts protected by two-factor authentication, so they needed a new attack method that could be deployed cheaply like phishing via the wide nets of automated spam.
So, they came up with the clever idea of consent phishing where instead of tricking a user to give them a password, they would trick a user into giving another application access to their Microsoft 365 content (email, calendars, contact lists, OneDrive documents, etc). You can read more about the details and how it works in Microsoft’s security blog post, but the way the attack is delivered is very similar to normal phishing attempts. A malicious actor tricks the user into clicking a link. But, that link takes you to a real Microsoft 365 page that asks your permission to give an app access to your content. Because it is a real Microsoft URL that displays the permission request, users may be inclined to accept the permission request. The prompts look similar to this:

Once the permissions are granted, the attacker can use the app to read through your data to steal information and/or social engineer additional attacks. The basic defense response and end-user education is simple: Don’t give third-parties or apps access to your data. But, it can be easy to trick a user into accepting some apps if it looks like it is coming from a “secure email” system, a file sharing utility, a marketing utility, a payment processor, or maybe even something from “your IT department”. The possibilities are endless and can easily be tailored to a users’ role in the business. And let’s face it, we’ve all been caught clicking OK on a prompt without fully reading the notice.
Thankfully, Microsoft has made it easy to fight consent phishing in Microsoft 365. In fact, if you are a maintenance customer, we implemented consent phishing protections back in July. Microsoft’s recommendation is to only allow users to consent to app publishers that have been verified by Microsoft in Azure Active Directory -> Enterprise applications -> Consent and permissions -> User consent settings.
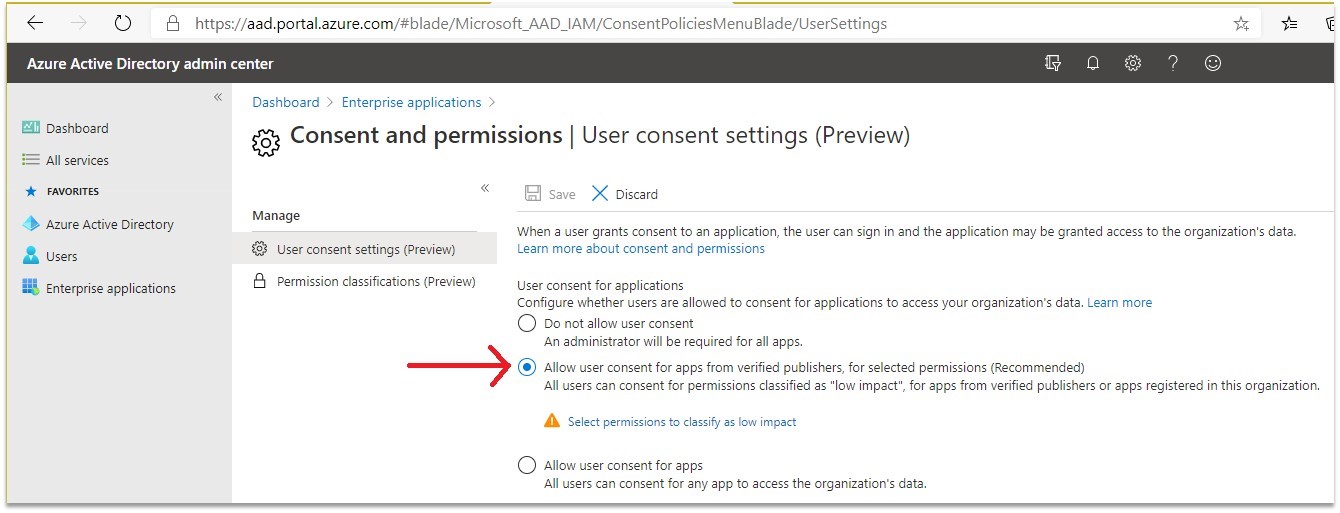
Combining this approach with limited user privileges, two-factor authentication implementations, and disabling legacy authentication and the services that need them like POP/IMAP/SMTP is a good start to protecting your users and data from the most common threats. Check out Microsoft’s article on securing your identity infrastructure for more ideas. Just make sure you remind your users to not accept permission requests from apps online.
Related Articles