

We believe the best line of defense against a security event is educating staff with best practices.
We believe the best line of defense against a security event is educating clients on best practices. Articles like Protect yourself from email scams and What Is Phishing? have educated our clients on how to identify and stop some threats right away. This is just the tip of the iceberg with the various ways bad actors attempt to exploit people. Another possible attack vector is malicious code embedded in files. So, what can you do if you have receive a file attachment on an email or a file to download from a cloud provider (Dropbox, ShareFile, etc) from a trusted source? We strongly recommend that you use the TrendMicro Security Agent to scan the file for any malicious threats before opening it. The steps below walk you through this process and again we recommend running through these before you open the files.
1. Locate the file on your computer, single right-click, and choose “Scan for Security Threats”.
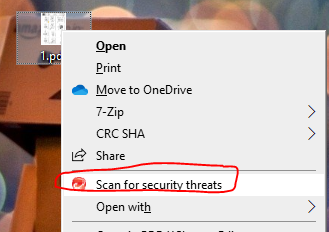
a. If you download from the internet, your web browser probably stored the file in your downloads folder. You can access it by opening windows files explorer and clicking the downloads shortcut in the menu on the left.
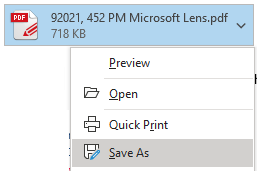
b. If the file is located in your email as an attachment, you will need to save it to your computer first by clicking the down arrow to the right of the attachment and choosing “Save As”.
2. Wait for the scan to complete and you should see 0 threats identified. Select “close”.
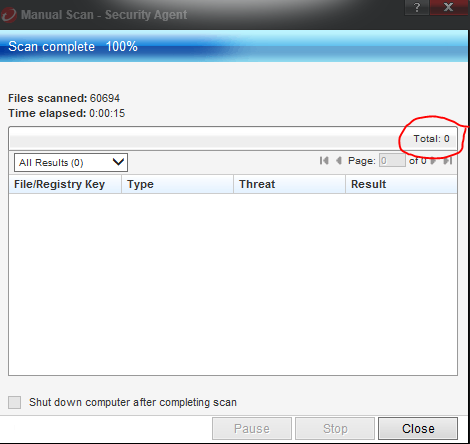
3. Please keep in mind that just because the file passes a security scan for malicious code, it is not guaranteed to be safe. But, you should feel confident enough to open the file at this point and investigate its content yourself. If the file immediately takes you to a page or link that asks for your Office 365 email or other password, it is probably trying to trick you into giving them your password. This type of threat is not always caught by the file scanner, so do not proceed with supplying a username and password at this point and close the file. You must first confirm with the sender that the file is legitimate using a method other than email. If the file is malicious, then the sender’s account was probably compromised and the hacker may still be monitoring it, so email communication is not safe.
We understand many of you have encountered unique work environments since the pandemic and we hope that these tips and tricks help no matter where you are located.
Related Articles