

If you have used the Microsoft Authenticator app on your cell phone recently, you may have noticed that the authenticator app now asks you to enter a two-digit number instead of just tapping “approve”. The screens look something like this:
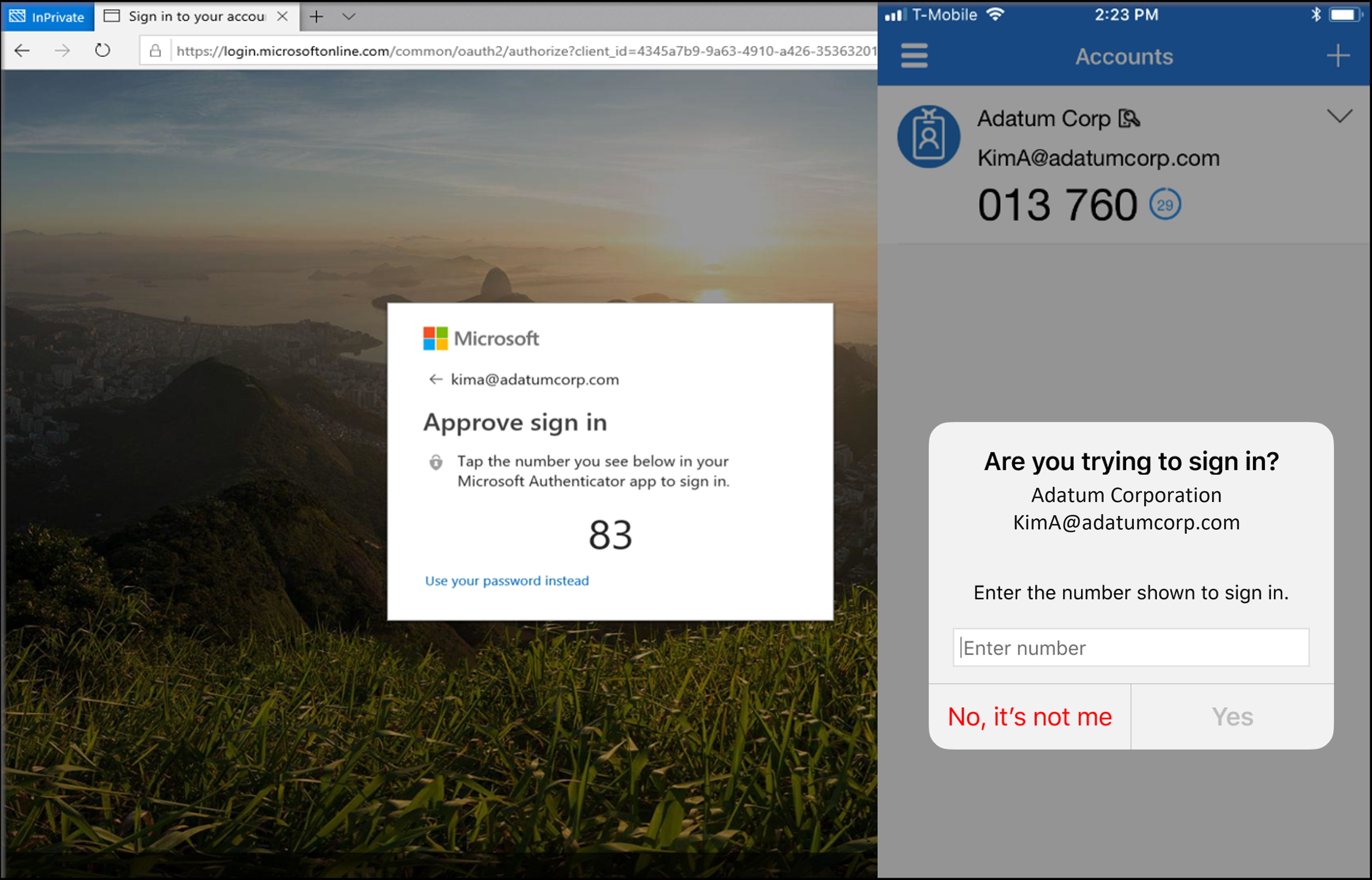

Source: https://learn.microsoft.com/en-us/azure/active-directory/authentication/how-to-mfa-number-match
Why did Microsoft do this?
Several high profile hacks have used a method called “MFA Fatigue” or “MFA/Push Bombing” to get unsuspecting victims to approve multifactor authentication attacks. The hackers will send dozens or even hundreds of approval prompts in a short period of time to trick us into tapping approve to just “make it stop”. In fact, ars TECHNICA reports that a leader in a large international hacking group described their approach by saying:
“Call the employee 100 times at 1 am while he is trying to sleep, and he will more than likely accept it. Once the employee accepts the initial call, you can access the MFA enrollment portal and enroll another device.”
As usual, hackers have found a way to manipulate our impulses to get what they want. So, Microsoft has developed the two-digit “number matching” approach to prevent this type of attack. It is a clever adjustment that keeps us secure without complicating the login process any further. But if you ever find yourself getting MFA bombed, just put your phone on silent, change your password, and let your IT contacts know so they can investigate.
I’m sure some of you are thinking that this isn’t much different than entering the 6-digit codes from a text message, email, phone app or token keychains. And you are kind of right, but this new process still keeps the login quick and easy while seriously stepping up security over getting codes via unencrypted channels. SMS text messages are one of the least secure methods of multifactor authentication because they aren’t encrypted and it is far too easy to clone or steal your phone number or SIM card. While using text messages for codes is better than not using multifactor authentication at all, it really isn’t secure enough to protect your data from a targeted attack. In fact, hackers love using SIM swapping techniques to gain access to bank accounts and crypto currency wallets for a quick score. TechRepublic has a good article and video that further expands on the flaws in using SMS text messages.
For those of you that use the DUO app for multifactor authentication, they have taken a different approach and battle MFA/Push bombing attacks by quarantining and blocking sign-ins on accounts that receive several MFA requests in a short period of time. It is a different approach, but as long as the user chooses to deny or ignores the prompt completely, the attack will be blocked, the user remains protected, and the DUO administrators are alerted to the attack by DUO for a quick response.
Did you forget to setup or transfer the Microsoft Authenticator app to a new cell phone or you want to switch away from text based multifactor authentication? Just go to https://aka.ms/MFASetup and it will walk you through adding the authenticator app as a new sign in method for your Microsoft 365 account. If you are switching the app to a new phone and don’t have the old one, you can still probably use the “sign in another way” link on the login screen to authenticator with a text message or a call. But, that may not continue to be an option in the future.
We hope you now have a better understanding of why the Microsoft Authenticator application works the way it does and why it is more secure than using other forms of multifactor authentication.